Identity Management
A quick overview of some different issues that exist when discussing identity management, and in which environments using SCIM could be relevant.
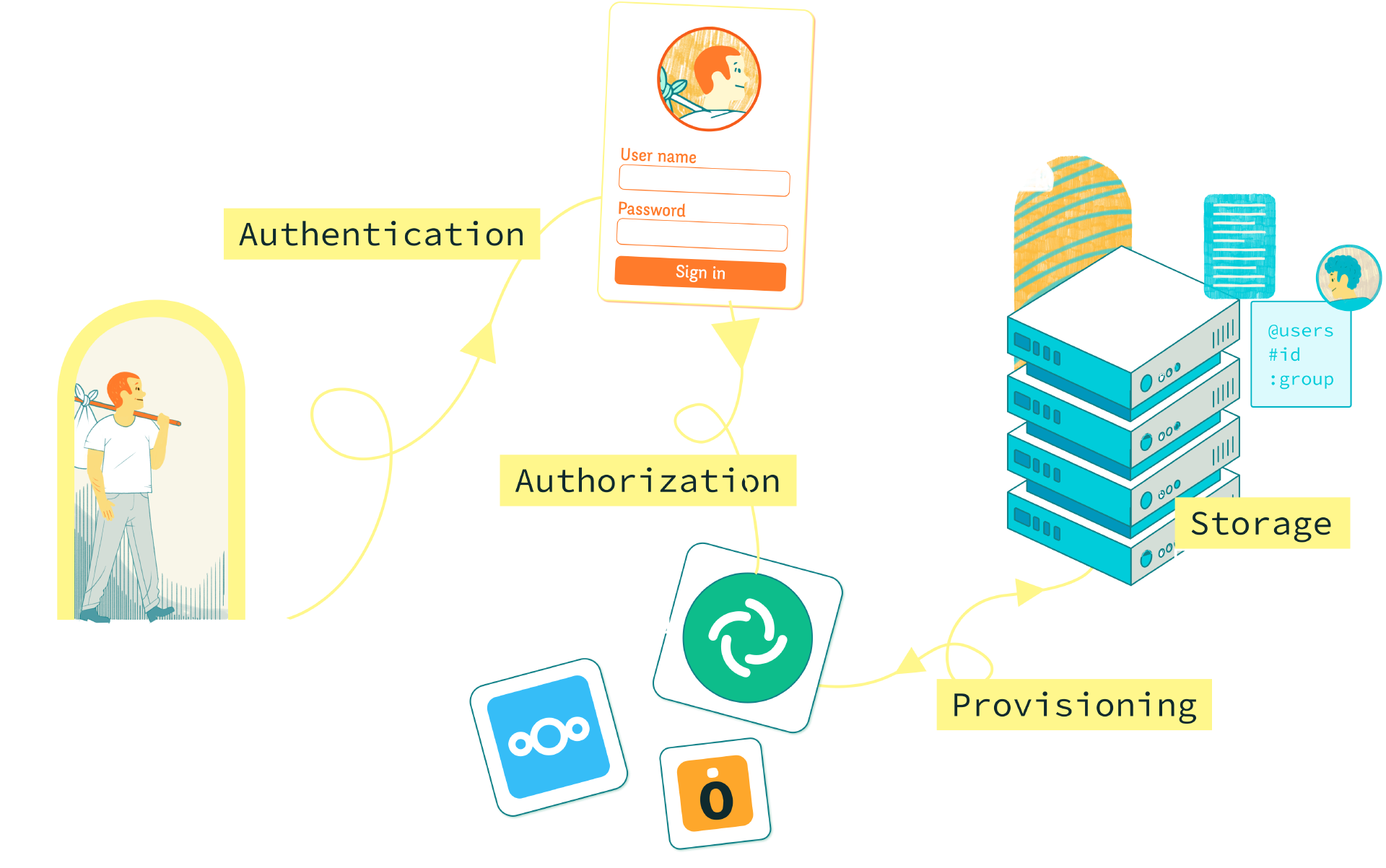
Authentication
Who is this user ?
Authorization
Is this user allowed to access this resource ?
Storage
Where are user’s identity & credentials stored?
Provisioning
How to manage & transfer user’s identity ?
Among all these identity management concepts, SCIM is a matter of provisioning ; it concerns how information linked to an identity is transferred between different apps.

SCIM environement
Because SCIM tackle the question of provisioning, one of best the identity management environments where SCIM is relevant is an environment composed of many apps or services that are not well integrated natively and are used by many users.
To better understand, let’s consider the use case of a hosting provider that develops a collaboration platform based on different free software.
The digital work environment is then composed of many applications and web services used by different users. These users want a seamless user experience across the different apps.
With a Single Sign-on (SSO) system, users get a unified login and logout experience but there is a catch.
The problem
Traditional SSO protocols like OpenID Connect do not support syncing user profiles across applications. That’s means :
- users are not created by default in all apps (only after they have logged in at least once)
- no mechanisms to propagate the deletion of users
- So its not GDPR compliant (by default)
In essence
Current existing protocols are difficult to implement or/and to use or are custom for specific use case then non-standardized.
The solution, SCIM
SCIM, for System for Cross-domain Identity Management are specifications designed to make managing user identities in cloud-based applications and services easier.
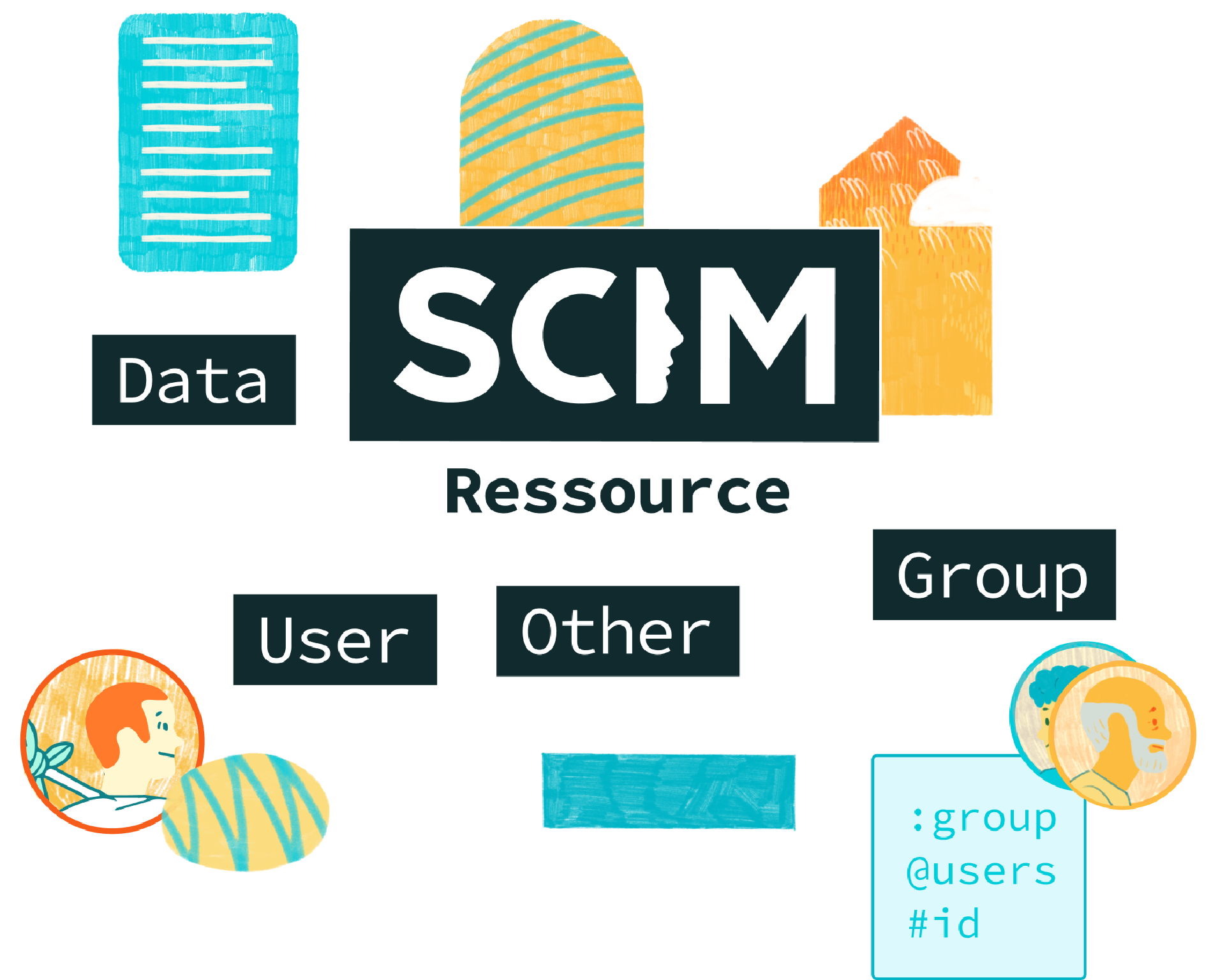
Quick overview
The SCIM protocol is an application-level protocol for provisioning and managing identity data specified through SCIM schemas. Its intent is to reduce the cost and complexity of user management operations.
- A common existing user schema and deployments
- Extension models
- Placing specific emphasis on simplicity of development and integration
- Applying existing models (authentication, authorization, and privacy)
- Binding documents to provide patterns for exchanging this schema using standard protocols
- Easily improve GDPR compliance
- Consolidate the user experience across multiple FOSS applications as one platform
Resource based
In SCIM 2.0 a Resource is the common denominator and all SCIM objects are derived from it.
Rest API
An api to manipulate resources, from patching a specific attribute to doing massive bulk updates.
Ends points
SCIM provides three end points to simplify interoperability and discover features and details.
In essence
Make it fast, cheap, and easy to move users in to, out of, and around the cloud.
How to use SCIM?
An opinion on using SCIM to provide information such as mail, first name, last name, group… accross different application with an Identity Provider.
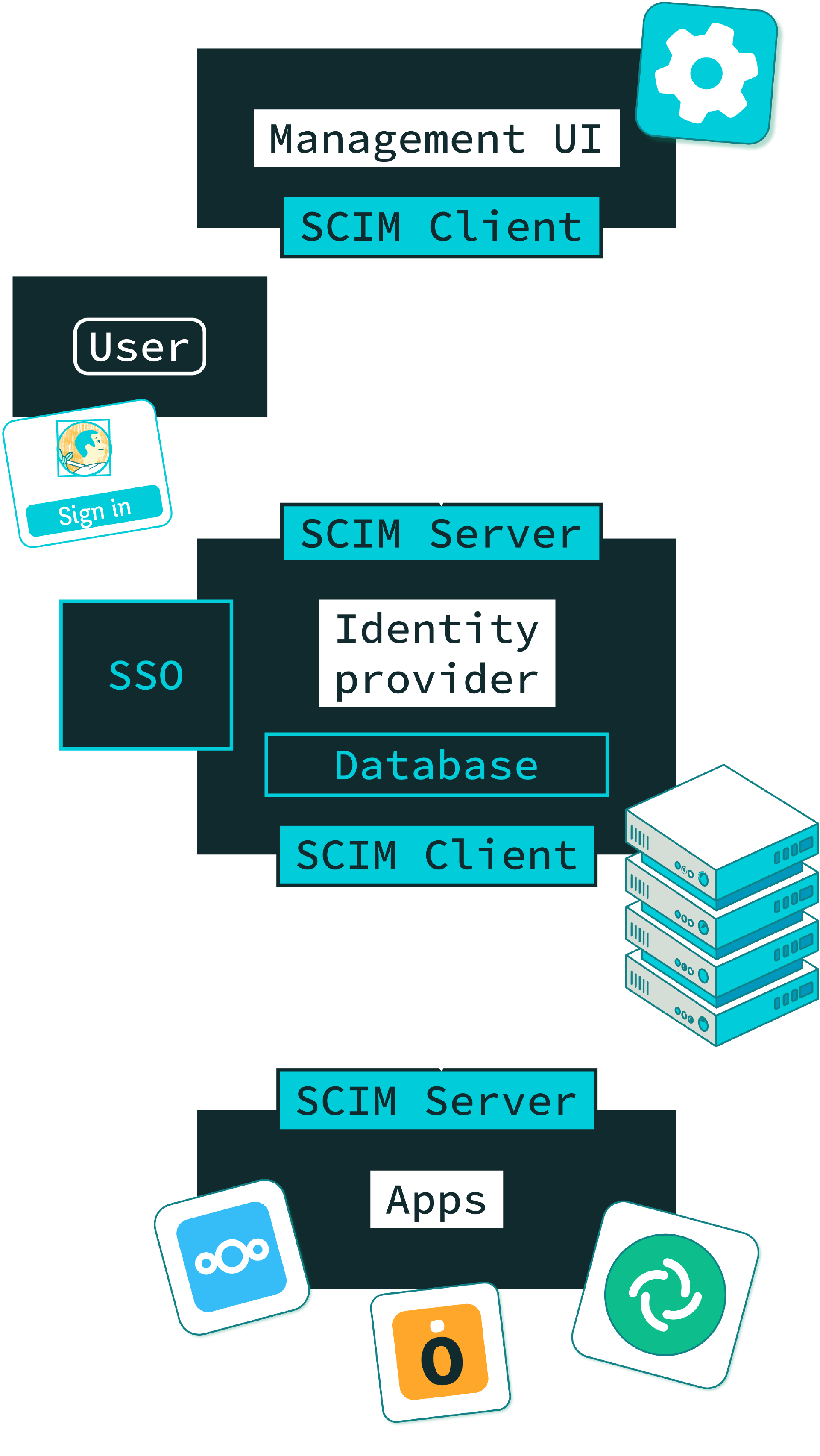
SCIM Client and Server
While SCIM is a protocol for provisioning and managing identity, there isn’t really a concept of Identity Provider (IdP) within its architecture. Instead, SCIM architecture consists (only) of a Client which makes HTTP calls, and a Server, which receives them.
An opinion on SCIM use A possible architecture could be as follows : a SCIM Client collocated with the Identity Provider reflects changes by calling all SCIM Servers collocated with each application.
With this architecture, there is a need for interoperability at 2 levels :
- between the user management UI and the IdP (the database where identity are stored)
- and between the IdP and the applications.
Thus, the IdP acts as both a SCIM client and server ; as a client when sending requests to apps and as a server when receiving requests from management UI.
How does it work ?
With SCIM protocol, clients can create, read, update, delete (CRUD) users and groups from a server.
In this scenario the standard SCIM API is used each time an user should be CRUDed in the Identity Provider.
And, when a resource is modified in the user database of the Identity Provider, the event is propagated to the configured applications. In this case the IdP becomes a client for these applications (which act as a SCIM Server in this scenario).
In essence
SCIM compliant open source Web SSO providers along with applications that support SCIM API for user provisioning could provide a seamless user experience.
Why is SCIM better ?
Differences between several centralized user management protocols in a world of web application hosting that show SCIM is an upgrade.
Others management protocols
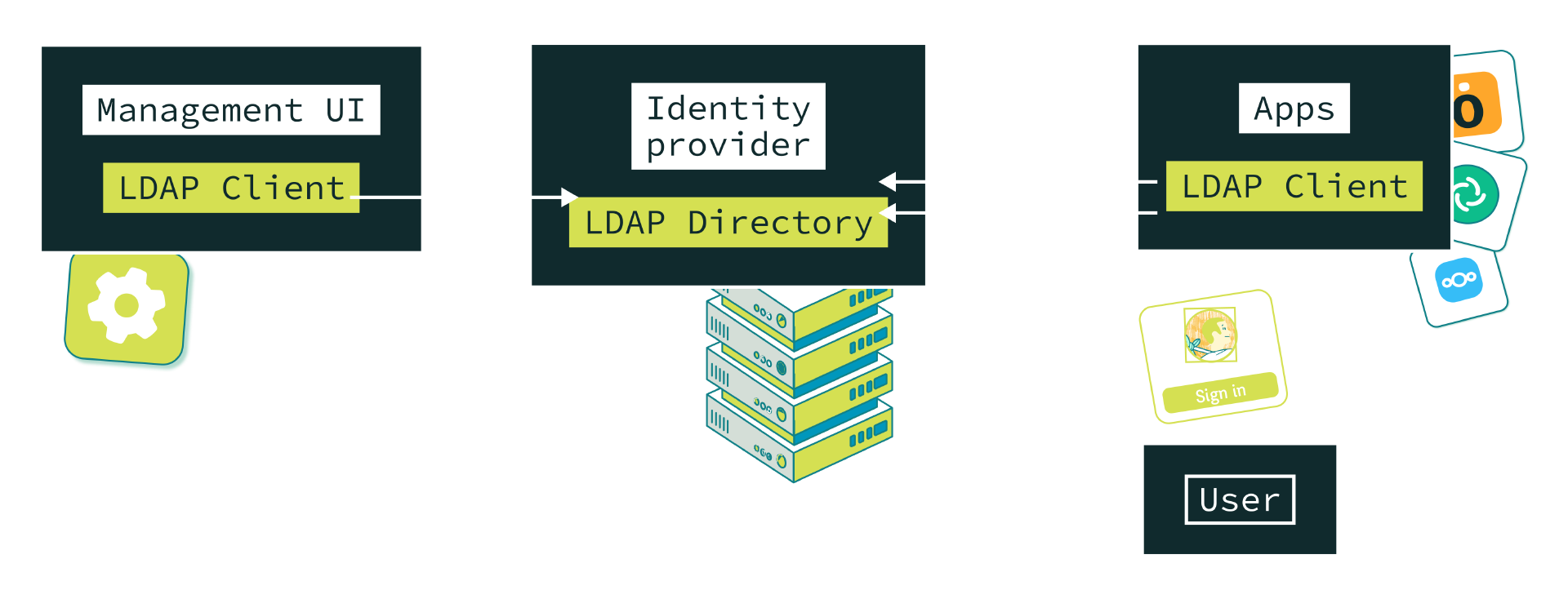
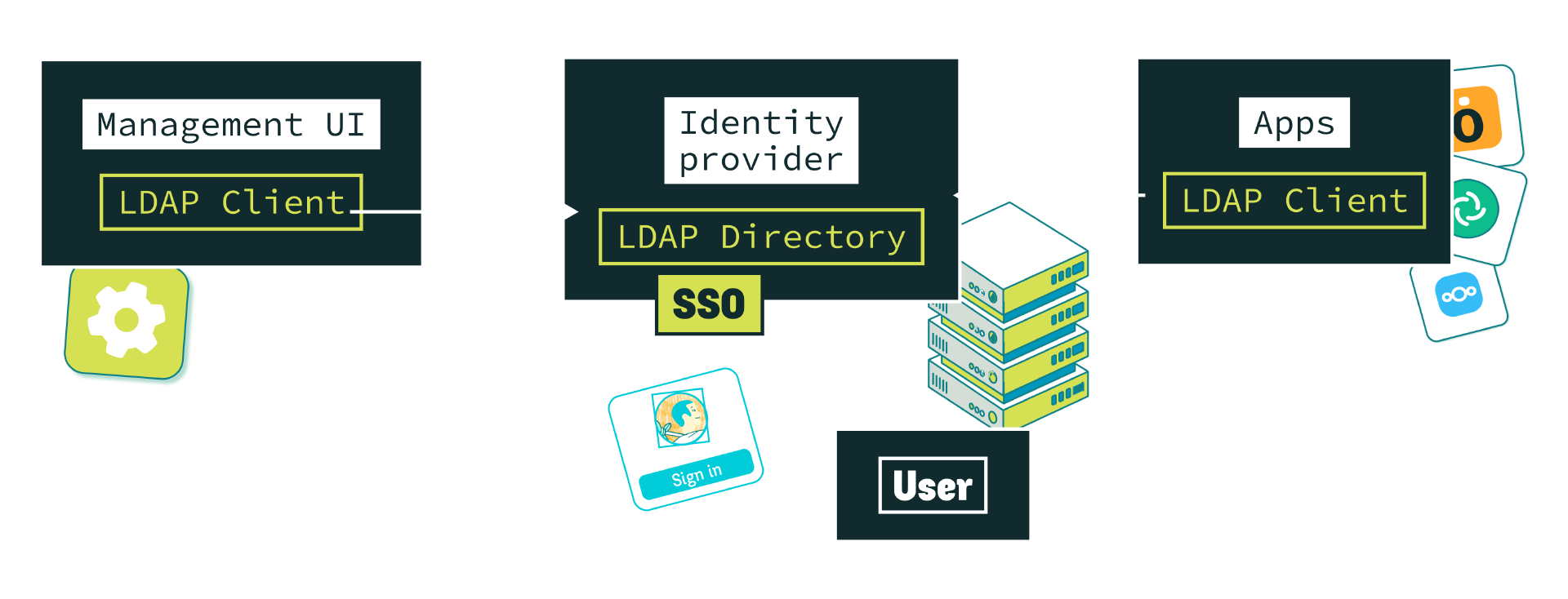
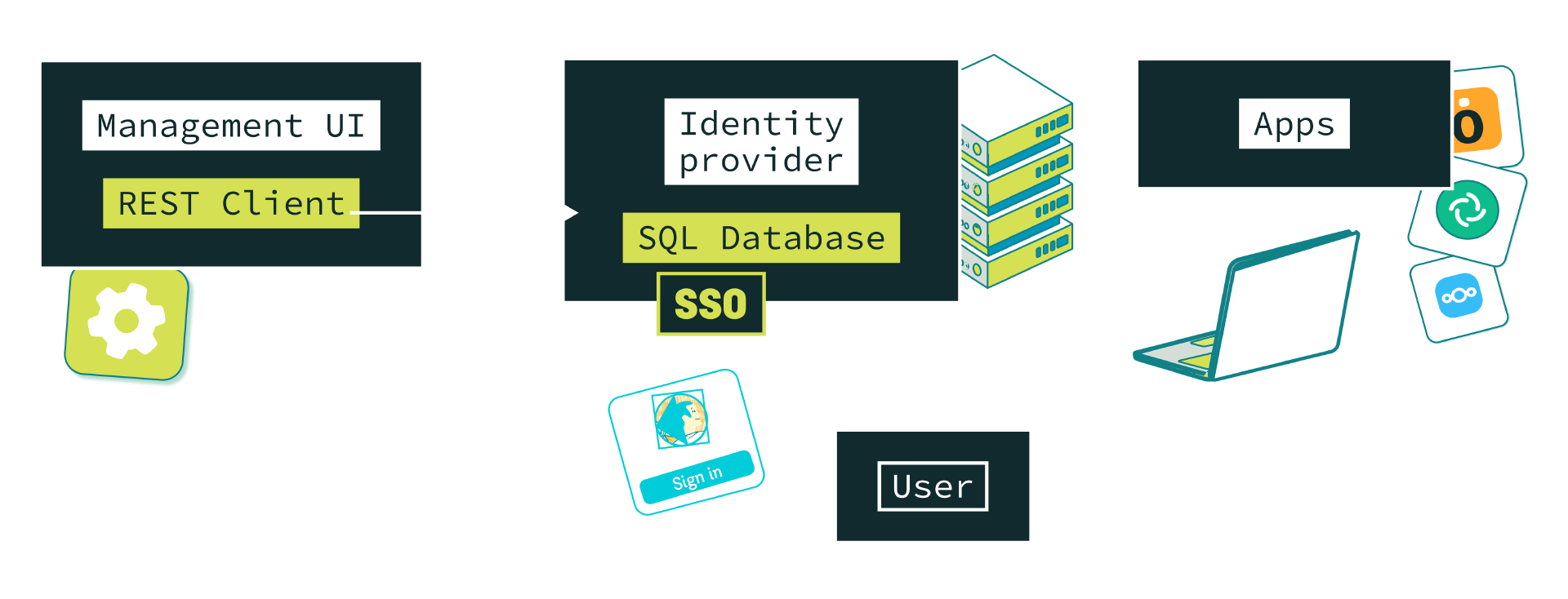
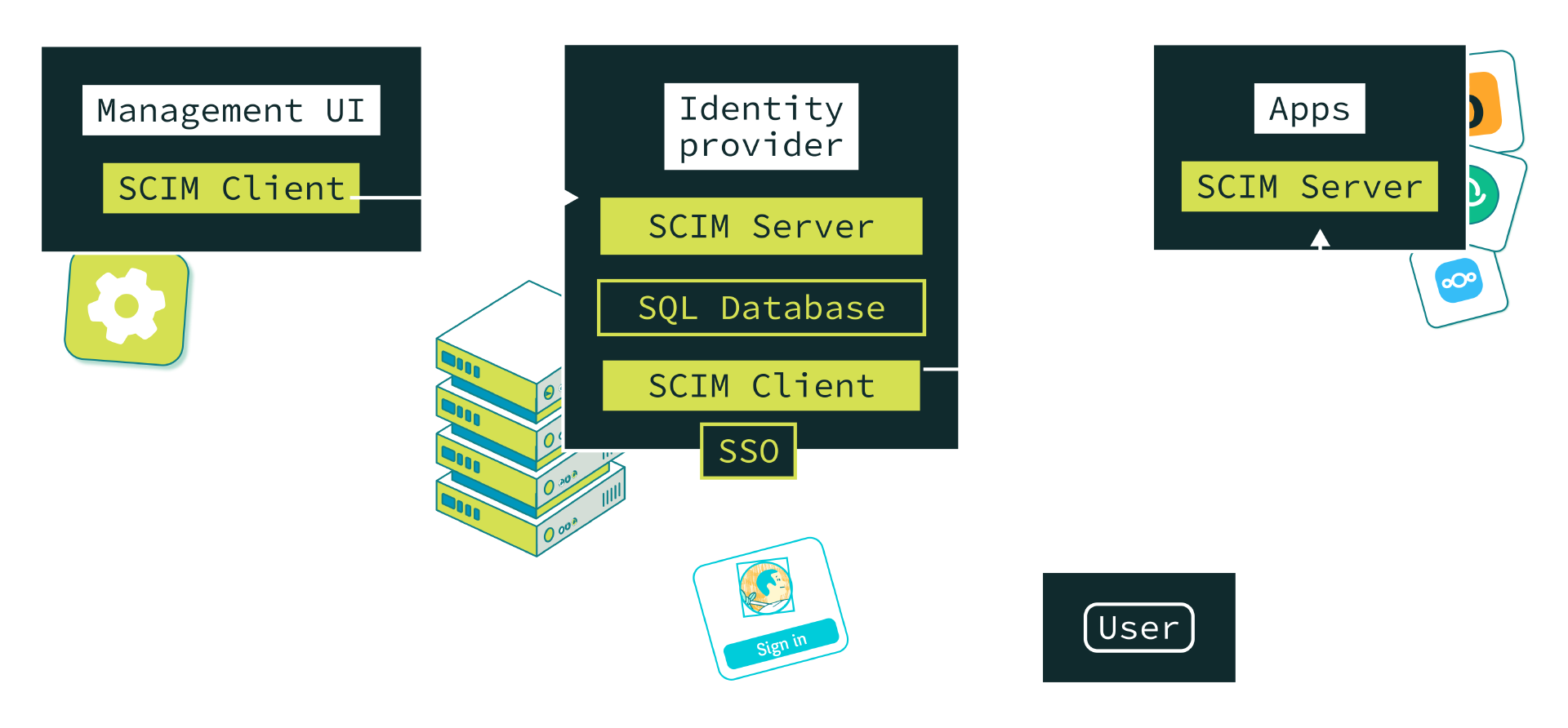
| LDAP | LDAP & SSO | SSO | SSO & SCIM | |
|---|---|---|---|---|
| Easy to implement | Mature but old and difficult | Mature but old and difficult | Simple and web native, but non-standard IdP | Cli or UI could be used on IdP or on apps |
| Many implementations | Not a lot of implementations yet | |||
| Single sign-on | User must sign-on each application | |||
| No trust issues | Expose user’s credentials to each application | Zero trust in applications | Zero trust in applications | |
| Scalable provisioning | By diffing, each app reads all and compares it | By diffing, each app reads all and compares it | No diffing, modern storage, SQL database can be used | Real time atomic provisioning |
| Scalable provisioning | Only when apps trigger it or when the user logs in | Only when apps trigger it or when the user logs in | No way to remove a user from the application | |
| GDPR Compliant |